Top 3 Ransomware Facts every Small Business Leader Should Know
Chelsea Sauder • February 20, 2020
According to SEC, 60% of small businesses go out of business within 6 months of a cyberattack. Ransomware is a particularly prevalent type of cyberattack which restricts businesses from their information until meeting certain financial demands – and sometimes even when you pay, you’re still locked out.
If you are a small business leader, could your business survive without access to your files, customer data, and documents? Could you overcome the financial impact of a ransomware attack?
The first step towards protecting your business is understanding the nature of the threat.
You may not pay the ransom, but you will pay the price of poor cybersecurity
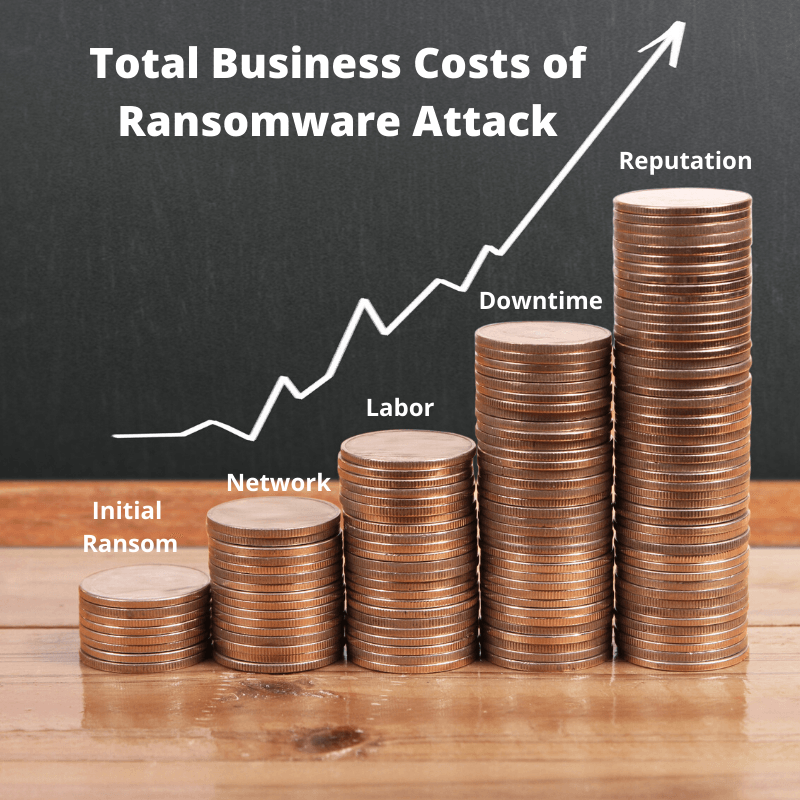
Most ransomware attacks ask for a payment between $500-$2,000, usually delivered via cryptocurrency or gift cards, which may seem a minor payout to some. The reality is that regardless of if the ransom is paid or not, a ransomware attack has a much larger financial impact.
According to SafeAtLast, the average cost of a ransomware attack on a business is $133,000. This amount accounts for the price of downtime, the network costs, and labor required to resolve the issue.
The one cost the above figure doesn’t take into consideration is the cost of your business reputation. In the event of a ransomware attack, if your system is inaccessible to consumers or sensitive information released during the attack is released, the credibility of your company may be put at serious risk. This is a very clear threat seen emerging in 2019 and 2020 – the new model is to steal your data first, and then encrypting it. You pay the initial ransom, and then you’re extorted every month to prevent that data from being publicly disclosed.
Evaluating the financial impact of ransomware requires a multi-factor analysis, but one thing is clear, whether you pay the ransom or not the overall cost to your company would be severe. Many insurance carriers require that you do not pay the ransom for your data breach insurance coverage to cover losses. Recently, New York state introduced a bill which, if passed, would prohibit state and local government entities from paying the ransom by law. The thinking is that if an attacker knows such an organization is barred from paying, they’ll choose another target. Only time will tell about the effectiveness of this approach; the imperative point is that ransomware is here and not going away.
Value is in the eye of the beholder
In today’s world, data is important. How data is collected, stored, transferred, used, and sold is a trending topic in both the business and political world. With today’s technology, even seemingly mundane information can be harnessed and used in a variety of ways – including cybercrime as a lucrative business model.
According to a recent survey, most small businesses say they do not prioritize budgets for cybersecurity and risk mitigation because they don’t believe they store valuable data. Upon further investigation, the survey revealed the majority of businesses store the below personal information:
Personal Data Stored by Companies
68% store email addresses
64% store phone numbers
68% store billing addresses
While that data may not seem of value to the business, this personally identifiable information (PII) is a prized resource to cyber criminals. When evaluating the worth of a company’s data, it is important to consider all potential parties that could be impacted by the information, including:
- The Company: To what extent does the organization use this data in normal business operations? If this data was no longer available would there be any risks or downtime? Are there legal ramifications for unauthorized data disclosure?
- The Consumer: Could the person related to this data be affected if the information was utilized outside of the agreed upon use? Is there data relating to minors?
- The Competitors: Does the sensitive data contain intellectual property or trade secrets which are vital to the success of the company?
- The Criminals: Could the data be used by cyber criminals to disrupt your business, target others, or distribute for financial gain?
It doesn't end with endpoint security
There is a general mindset with small businesses that keeping their devices up to date regarding operating system security patches is enough to get by. This is a common misperception – but it’s dangerously incorrect.
As technology continues to evolve, so do the techniques of modern cybercrime. SafeAtLast
reported that in 2018, more than 77% of the businesses affected by ransomware were using up-to-date protection on their devices.
Cybercriminals use several different methodologies to take your business hostage. Employees opening untrusted email attachments or clicking unverified links are indeed the most well known threat methods, but they’re far from the only way – and even then, it’s possible for ransomware to gain a foothold this way even with endpoint security solutions. Even the most careful can get encrypted. It only takes one mistake, and sometimes extremely small ones. It is far more important to have a tested recovery plan so you can resume normal business faster.
If you want to ensure a comprehensive security plan to defend and respond to ransomware threats, consider the following measures:
- Audit Your Business: Hire a third party to audit your company’s systems and identify potential weaknesses that could be exploited. We offer a low-cost solution designed for small businesses with our Ransomware Preparedness Assessment.
- Know Your Data: What type of data does your company use and where to different approaches: encryption-at-rest, privileged access, cloud storage, offline archival, etc.
- Train Your Staff: Set up a formal process to regularly educate your staff on cybersecurity. Better yet, partner with some accessible experts and combine knowledge with peace of mind.
- Carefully control the “keys to the castle”: In small businesses where everyone wears many different hats, it can be tempting to share usernames and passwords, or give multiple people free reign to the business. Take the time to work through separation of duties, and only grant access to sensitive data to those who require it to perform their job functions. Not because you don’t trust your people, but because for each person that has access, that’s an additional avenue for that data to be stolen, altered, or encrypted.
With this information you should realize the gravity of the situation when it comes to your business and ransomware. It’s here, it’s real, and ignoring it is dangerous.
At TexasPGB, our approach to cybersecurity
for small businesses is holistic, efficient, and affordable. Fill out the form below and let’s work together on a Ransomware Preparedness Assessment
to ensure you’ve got the best protection possible.
Share this post with others:
When it comes to automating processes around your business, it can simultaneously seem like everything can be automated, and absolutely nothing can be automated. As with many other things, the real answer is somewhere in the middle but can be a bit challenging to put your finger on. These projects usually start when someone at the strategic level of the organization has decreed that “we are going to automate!” and either they personally go on the hunt for what to automate or they hand it off to someone on their team to go do the leg work and come back with “automation” (maybe in a nice box with a bow on it). Sound familiar?

Data is everywhere. You’ve got a lot to focus on and it can be hard to stay on top of what’s going on with your business. Report creation in Excel is often time-consuming and can quickly become a nightmare. Modernizing your reports and streamlining your process with PowerBI to get more reliable and consistent reporting across all of your systems can be a game changer for your business. Read on to learn about three key acceleration tactics that our team uses on every implementation that we facilitate.

83% of knowledge workers require technology to work together. Microsoft Teams is a cloud-based collaboration and communication tool that lets workers share the right information to the right people all through one integrated platform. According to a Forrester report, The Total Economic Impact of Microsoft Teams, there are a variety of ways using Teams saves organizations time and money. Read and download the infographic to share here .
How to Get Started with the Power Automate app for Teams You can get started with Power Automate app in just 3 quick steps: Click on the … in the left-hand corner of your teams browser Search for “Power Automate” Click on the Power Automate app icon and pin it to your left-hand Teams navigation panel
As mentioned, there are several options available for automating your business. One of our favorite low-code/no-code options is the Microsoft Power Platform. As a suite of 4 different tools, the Power Platform can automate routine tasks, customer support, data visualization, and more. A few highlights on the effectiveness of the Power Platform are:

It is no secret that 2020 and the coronavirus pandemic altered the reality of doing business. These changes are showing little signs of letting up and a lot of the adjustments made to respond to a remote workforce may very well become a permanent feature in daily business operations. As business decision makers (BDMs) and IT decision makers (ITDMs) head into a new year it is important to keep an eye out for technology solutions that can further support these operational changes while increasing efficiency. This post briefly highlights the top 3 digital solutions we have our eyes on for 2021 and our Microsoft-based clients.

In our latest video series, Patrick Boren, Principal Consultant at TexasPGB, introduces the newest addition to the Microsoft Project family, Microsoft Project Operations. In this video Patrick discusses: What challenges Project Operations aims to solve What is Project Operations and common use cases for the tool Who uses Project Operations Upcoming "Day in the Life" Sessions Watch the video or read the condensed transcript below.
Having a wealth of data at your fingertips is great, but what happens when your data is so vast that it takes you years to make a key discovery? A friend of mine told me a story recently about an experience he had. His first company conducted a VP meeting every quarter – everyone scrambling to put together their presentations and make their case based on the data from Excel spreadsheets. Departments and information tended to be segmented into silos. While much of the data could be shared across the company, rarely was it compiled in a way to show how one area of the business could affect another.

If you are looking to migrate your data to Microsoft 365 there are two common methods to funnel your data - SharePoint or Common Data Service (CDS). SharePoint solutions take advantage of lists and libraries. Data is housed, originated, and manipulated entirely within the SharePoint platform. CDS solutions use both standard and custom entities to collect and house data that is then integrated across the Microsoft 365 platform. Below we will review a few ways each method is different and what you should look for before making a final decision for your data migration plan.
When it comes to technology, do you have a one-size-fits-all vendor? In today’s world of cost cutting, we see more and more organizations that end up missing out on huge technology opportunities by assuming a single vendor can and will do it all. As a technology consulting firm, we’re frequently asked “aren’t you the same as my managed service provider (MSP)?” Fortunately, for those that ask, we’re able to shed light on how a Technology Consulting Firm varies from an MSP.