Enabling Working from Home: 3 Awful Ideas and Their Alternatives
Chelsea Sauder • April 2, 2020
Many decisions within IT architecture, implementation, and policies (and more specifically, security) fall on a continuum: one end is strategic, proactive, secure, and leading innovation; the other is decisions which are reactive, rushed, and/or laden with risk. Since these decisions are a result of evaluating the relative risk versus the relative benefit, let’s consider this a quotient, and call the spectrum these decisions occupy The Q Continuum.
As the entire world deals with and reacts very quickly to COVID-19 and the mass adoption of working remotely, we’re seeing businesses enabling their newly remote workforce where only how quickly the solution can be deployed matters, without considering reasonable and appropriate security concerns.
Awful Idea #1: Corporate VPN on Home Computers
Connecting employee home computers to the corporate Virtual Private Network (VPN) is a common response to the sudden transition to a remote workforce. Some say that this is matter of necessity, as there just aren’t enough corporate laptops to issue every team member. While the shortage of company devices is indisputable, deploying remote workers this way is like inviting a couple hundred preschoolers with the sniffles over for a playdate and hoping none of the healthy kids get sick. This is a significant risk to your data and organization.
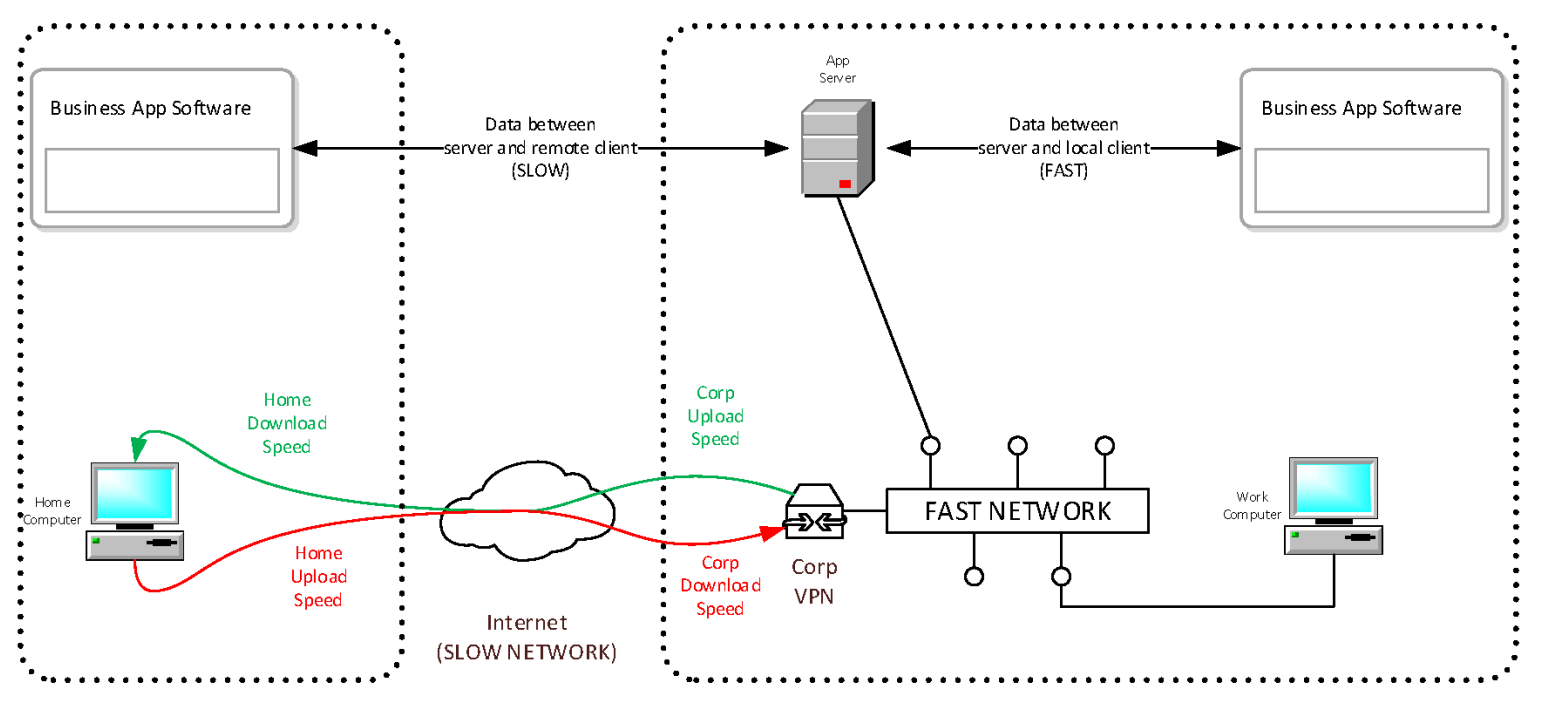
Let’s examine the components of a remote worker using their home system, fully connected by VPN:
Why it’s an Awful Idea
- Patches: Home computers range from “modern and fully patched/updated”. to “still running Windows XP” – and without interrogating each connecting machine, you have no visibility into the state of that device’s firewall, antivirus, or patches and updates. Even if you’re able to identify an issue in one of these areas, the best, you can do is prohibit that system from connecting to the corporate VPN – but that prevents your employee from doing their job. Since the system isn’t hardened or managed by IT, how would your organization bring your user’s home machine up to corporate spec and maintain it there? The effort compounds with more and more machines.
- Privileges: Home users are typically local administrators on their personal systems and have unrestricted access. This leaves them more susceptible to malware, a great deal of which needs administrative access to infect a system. The older the home machine’s operating system is, or the farther behind it may be on security updates, the bigger this threat is. If a home computer gets infected with malware and is later connected to the corporate VPN, the entire network can be compromised.
- People: Home systems may have multiple accounts configured for different members of a family, and it’s likely they’re all administrators. This means a security compromise of a user not at all related to your organization can be leveraged against your business, just by a computer having an active VPN session.
- Performance: Providing home computers full VPN access to your corporate network can result in poor performance for the individual user because of the business application traffic between the remote computer over the relatively slow Internet. If you happen to have asymmetric upload/download rates, having multiple users do this at the same time can overwhelm the upload bandwidth at the corporate end. This simultaneous activity can slow down the VPN for everyone.
Do This, Not That
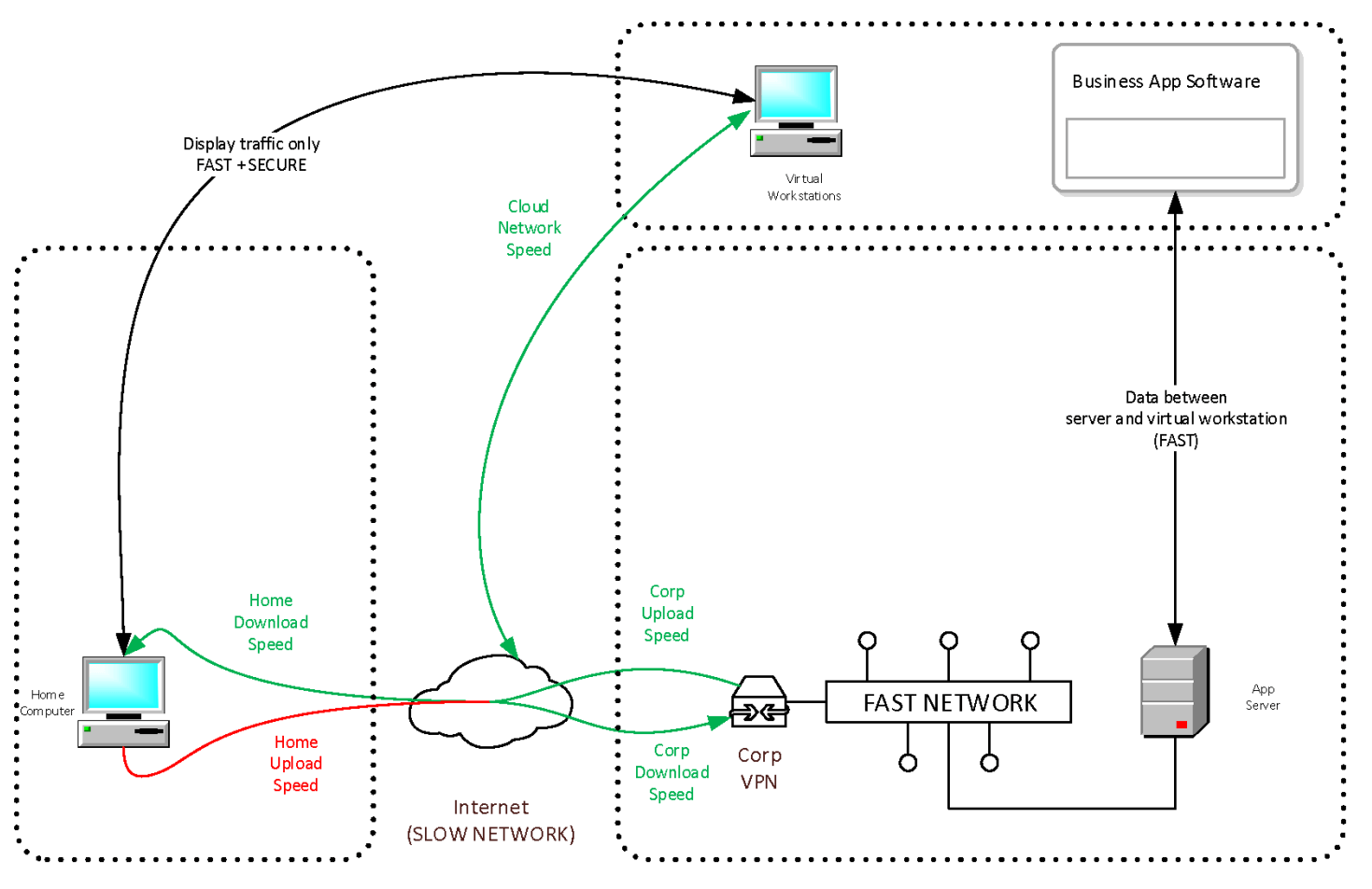
You don’t want this huge variety of unmanaged systems to be able to reach out and touch your work technology resources. There’s a better way – Virtual Workstations.
The benefits are reduction of security risk, more efficient data transfer meaning better performance of your apps, and a faster, less frustrating experience
for your remote workforce. These virtual layers support audio and cameras, so yes, your people can even use video conferencing tools like Zoom.
This better way still allows your people to use their home computers to do work, but only permits use of the home computer as a remote-control display of a virtual computer that is protected as a company technology asset. This method insulates you from home computers (that horde of sniffling preschoolers!) reaching out to your IT resources directly. It also neatly gets around the problem of limited upload bandwidth common to home internet services. Let our awesome datacenter take care of the heavy lifting while you focus on running your business. Your people can still connect to your office VPN from their virtual computer if required.
Let’s dive in to how this works: you give your users an entire virtual computer to work with, or you can deploy only those business applications people need based on their jobs. With TexasPGB, we deploy these as needed, from our local datacenters for the best performance, which drastically improves applications using voice and video. our people get a responsive, performant computer to be effective at their job. In turn, you get peace of mind knowing that their virtual computer is under the security controls of your organization, and your technology and data is protected from potentially very dangerous home computers.
Our Virtual Turn-Key service includes:
Awful Idea #2: Remote Desktop (RDP) on the Internet
Remote Desktop Protocol (RDP) is a client/server protocol developed by Microsoft which gives a user a graphical user interface (desktop) over a network, including the Internet. RDP server software is built-in to Windows and available for Mac and Linux systems.
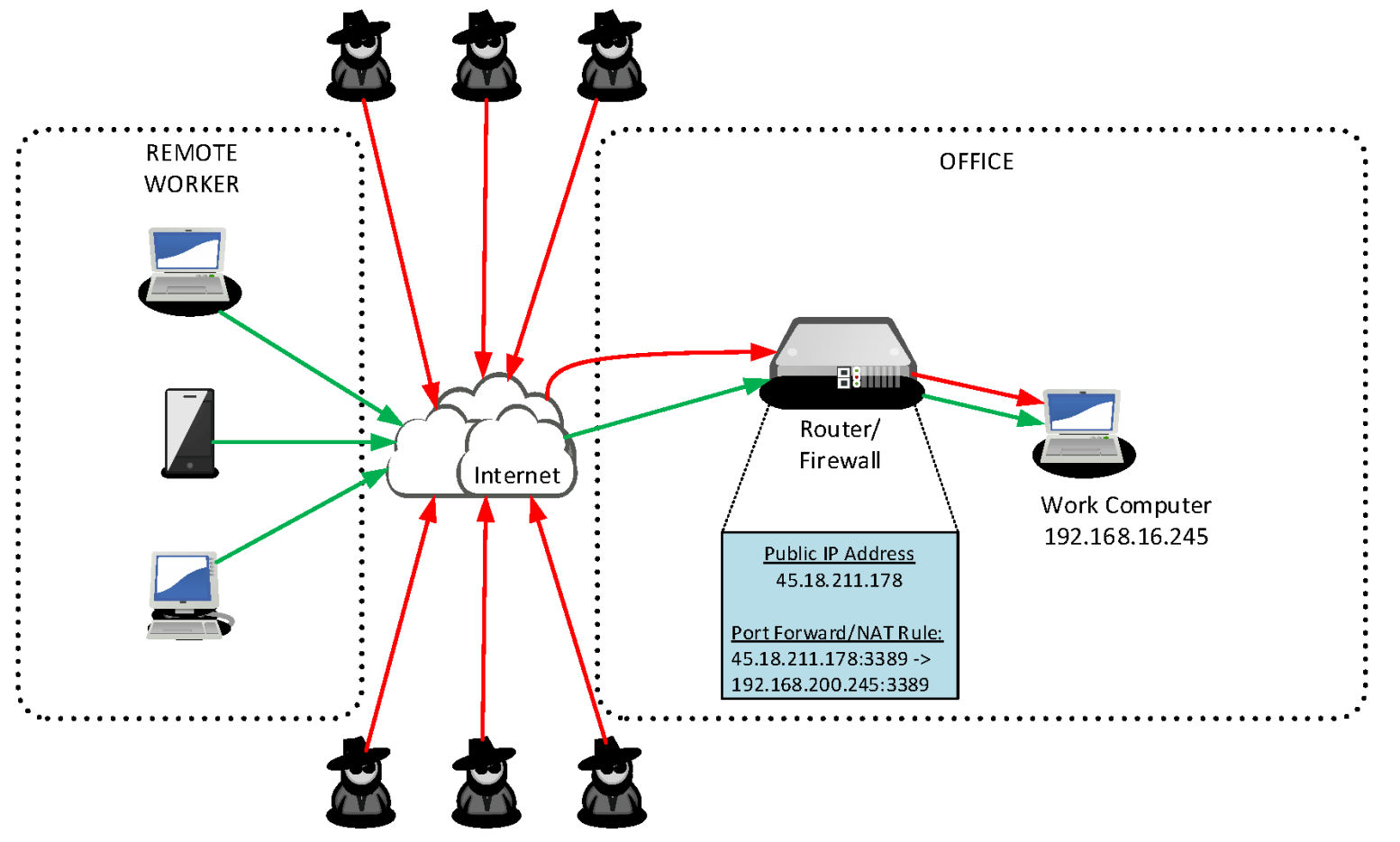
Allowing incoming RDP connections to specific servers or desktop computers can be achieved by IP NAT commonly known as “port forwarding” on a router or firewall which is directly connected to the Internet. By default, the RDP server listens on TCP port 3389. The administrator of the internet facing router configures it such that specific network traffic inbound from the Internet is directed to one or more computers, each running the RDP server. The remote user simply connects their Remote Desktop Client to a hostname or IP address, and sometimes a specific TCP port, and the router bridges their connection to the desired computer running an RDP server. Unfortunately, the same method is easily used as well by anyone else on the Internet, and they’ll come along in great numbers to twist on your doorknob.
This scenario has become very common lately with the giant increase in remote working because it is quick to implement, and when connecting to Windows RDP servers, free.
Why it’s an Awful Idea
RDP has had a number of significant security flaws since its inception, and while most of those have been mitigated and patched, it was less than a year ago that CVE-2019-0708 – better known as BlueKeep – was discovered. BlueKeep allows an attacker to run any bit of malware or ransomware they wanted, and it is theoretically wormable, meaning an infected computer goes to work infecting any other computers it can.
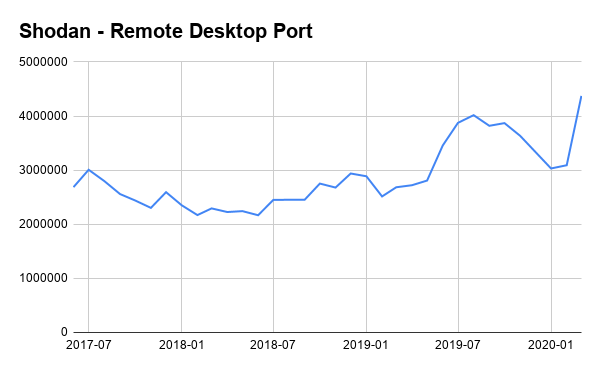
According to Shodan, a specialized search engine that reports on specific types of computers and devices connected to the Internet, the number of computers exposing RDP directly has increased by 41% in March 2020.
This is terrifying news for cybersecurity. These millions of computers accessible to anyone on the Internet are usually protected only by a username and password, and by default do not do anything to block or even notify their administrators of attempted brute force login attacks.
- Many people, despite education attempts, use the same password for everything, or use passwords which are very easy to guess.
- Some cloud services - Microsoft Azure – use RDP by default for remote access to Windows virtual machines, and many people provision their Azured Network Security Group (NSG) to permit port 3389 without locking it down to a specific set of IP addresses.
- The popular data breach tracking website haveibeenpwned.com knows of over 9.5 billion accounts which are compromised from breaches. While they don’t share the usernames and passwords, the fact they have them means those accounts and passwords are available to attackers.
- If an attacker correctly guesses just one of those millions of passwords – congratulations, they’re on your RDP server and inside business network just like they were sitting at that computer. It’s open season for data theft and ransomware infection.
This isn’t a complicated or new technique – current estimates suggest the average RDP server exposed to the internet is subject to 150,000 login attempts per week – that’s roughly 15 unauthorized login attempts happening every minute the computer is online!
There are established cybercriminal markets for stolen RDP credentials and compromised computers. Local governments of cities, hospitals, and utility providers have all been victim to targeted ransomware and theft-of-data attacks by this method.
It doesn’t matter if you use port 3389 or a different port to try and obscure it – the Internet is constantly scanned. Researchers at security firm Sophos conducted an experiment in July 2019 by placing 10 RDP servers on the Internet from points around the world. All of them were found within 16 hours – the first was found by attackers within just 84 seconds
of being brought online.
Do This, Not That
Work Remotely, Work Safely Today
RDP is a fantastic and cost-effective remote access tool, but you should absolutely not expose it directly to the Internet. If your RDP is currently exposed to the Internet, you should stop doing that as quickly as possible. Some smarter ways to provide your people remote access to RDP:
- Consider deploying a VPN solution for your users and launching their RDP connection after connecting to the VPN. Even an opensource/free VPN solution will do better than direct RDP.
- Deploy Microsoft Remote Desktop Gateway on your server to accept secure connections from the Internet over https and then function as a proxy between the remote users and the internal RDP servers. This doesn’t require a separate VPN solution so it’s easier for the users. Bonus: it can be integrated with multi-factor authentication. It’s a great choice if all you have is one server and your router doesn’t support VPN clients.
- Are you exposing multiple ports because different people need to RDP to different computers in your office? Call us – we can help you with a clientless web portal so each person can securely RDP to their particular computer, with just a web browser.
Awful Idea #3: TeamViewer / LogMeIn / GoToMyPC / Splashtop
Third party remote access tools are becoming increasingly prolific, including products like TeamViewer, LogMeIn, GoToMyPC, Splashtop, and many others. The attractiveness of these tools is that they’re easy and quick to deploy. However, they all share one common thing: both the server computer and the client device must send their traffic out to the Internet via cloud servers maintained by the vendors.
Why it’s an Awful Idea
This means that just like in idea #2, any client on the Internet can potentially access them with a simple username and password. With TeamViewer for example, all that is needed for a default installation is the hosting computer’s partner ID (10 digits) and a randomly generated 6-character password consisting of 3 numbers and 3 letters, all of which are lower case. This is paltry password strength. TeamViewer does offer additional authentication options – Easy Access, where access is granted only to a logged in TeamViewer account, which hopefully has a stronger password. Or, you can create a Personal Password – but again, the default length is 6 characters, purported as “secure” by the TeamViewer software. A final choice is to enable Windows authentication where the connecting client uses the destination computer’s normal username and password.
It is also worth noting that the free version of TeamViewer is not permitted for commercial use.
Do This, Not That
In the above example citing TeamViewer, it is possible to enable multi-factor authentication. It must be done with an account on teamviewer.com and is not enabled by default. This and many other security features are not enabled by default, which makes it entirely too easy to deploy TeamViewer in an insecure manner, which puts remote access to your business at risk. The fact is that anyone on the Internet can have a computer automatically iterate through a list of 10-digit number combinations and attempt to brute force guess the password, with a high likelihood that it consists of 3 numbers and 3 lower case letters. This configuration is arguably less secure against brute force login guessing attacks than putting RDP on the Internet, covered in idea #2.
What we recommend instead of these 3 awful ideas, is to implement a remote access solution which gives your remote personnel the ability to do their job and be productive but doing so in a manner that is mindful not to introduce unacceptable security concerns and risk to your business and its data. There are many different options to enable a remote workforce and the best solution will vary based on your organization’s needs. Instead of rushing towards the easiest remote access solution, taking the time to determine and implement the right solution, supported by technical experts, can mean the difference between security and data theft.
Let us help you navigate technology challenges. Contact us today
to leverage our knowledge and expertise.
Share this post with others:
When it comes to automating processes around your business, it can simultaneously seem like everything can be automated, and absolutely nothing can be automated. As with many other things, the real answer is somewhere in the middle but can be a bit challenging to put your finger on. These projects usually start when someone at the strategic level of the organization has decreed that “we are going to automate!” and either they personally go on the hunt for what to automate or they hand it off to someone on their team to go do the leg work and come back with “automation” (maybe in a nice box with a bow on it). Sound familiar?

Data is everywhere. You’ve got a lot to focus on and it can be hard to stay on top of what’s going on with your business. Report creation in Excel is often time-consuming and can quickly become a nightmare. Modernizing your reports and streamlining your process with PowerBI to get more reliable and consistent reporting across all of your systems can be a game changer for your business. Read on to learn about three key acceleration tactics that our team uses on every implementation that we facilitate.

83% of knowledge workers require technology to work together. Microsoft Teams is a cloud-based collaboration and communication tool that lets workers share the right information to the right people all through one integrated platform. According to a Forrester report, The Total Economic Impact of Microsoft Teams, there are a variety of ways using Teams saves organizations time and money. Read and download the infographic to share here .
How to Get Started with the Power Automate app for Teams You can get started with Power Automate app in just 3 quick steps: Click on the … in the left-hand corner of your teams browser Search for “Power Automate” Click on the Power Automate app icon and pin it to your left-hand Teams navigation panel
As mentioned, there are several options available for automating your business. One of our favorite low-code/no-code options is the Microsoft Power Platform. As a suite of 4 different tools, the Power Platform can automate routine tasks, customer support, data visualization, and more. A few highlights on the effectiveness of the Power Platform are:

It is no secret that 2020 and the coronavirus pandemic altered the reality of doing business. These changes are showing little signs of letting up and a lot of the adjustments made to respond to a remote workforce may very well become a permanent feature in daily business operations. As business decision makers (BDMs) and IT decision makers (ITDMs) head into a new year it is important to keep an eye out for technology solutions that can further support these operational changes while increasing efficiency. This post briefly highlights the top 3 digital solutions we have our eyes on for 2021 and our Microsoft-based clients.

In our latest video series, Patrick Boren, Principal Consultant at TexasPGB, introduces the newest addition to the Microsoft Project family, Microsoft Project Operations. In this video Patrick discusses: What challenges Project Operations aims to solve What is Project Operations and common use cases for the tool Who uses Project Operations Upcoming "Day in the Life" Sessions Watch the video or read the condensed transcript below.
Having a wealth of data at your fingertips is great, but what happens when your data is so vast that it takes you years to make a key discovery? A friend of mine told me a story recently about an experience he had. His first company conducted a VP meeting every quarter – everyone scrambling to put together their presentations and make their case based on the data from Excel spreadsheets. Departments and information tended to be segmented into silos. While much of the data could be shared across the company, rarely was it compiled in a way to show how one area of the business could affect another.

If you are looking to migrate your data to Microsoft 365 there are two common methods to funnel your data - SharePoint or Common Data Service (CDS). SharePoint solutions take advantage of lists and libraries. Data is housed, originated, and manipulated entirely within the SharePoint platform. CDS solutions use both standard and custom entities to collect and house data that is then integrated across the Microsoft 365 platform. Below we will review a few ways each method is different and what you should look for before making a final decision for your data migration plan.
When it comes to technology, do you have a one-size-fits-all vendor? In today’s world of cost cutting, we see more and more organizations that end up missing out on huge technology opportunities by assuming a single vendor can and will do it all. As a technology consulting firm, we’re frequently asked “aren’t you the same as my managed service provider (MSP)?” Fortunately, for those that ask, we’re able to shed light on how a Technology Consulting Firm varies from an MSP.